last updated: 04/11/2014 23:30 UTC
1) What is it?: http://heartbleed.com
"The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. This weakness allows stealing the information protected, under normal conditions, by the SSL/TLS encryption used to secure the Internet. SSL/TLS provides communication security and privacy over the Internet for applications such as web, email, instant messaging (IM) and some virtual private networks (VPNs).
The Heartbleed bug allows anyone on the Internet to read the memory of the systems protected by the vulnerable versions of the OpenSSL software. This compromises the secret keys used to identify the service providers and to encrypt the traffic, the names and passwords of the users and the actual content. This allows attackers to eavesdrop on communications, steal data directly from the services and users and to impersonate services and users."
2) Vulnerability: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
3) Security Advisory: https://www.openssl.org/news/secadv_20140407.txt
4) Patch: https://github.com/openssl/openssl/commit/96db9023b881d7cd9f379b0c154650d6c108e9a3
5) PoC exploits:
5.1)
http://www.exploit-db.com/exploits/32745/
http://s3.jspenguin.org/ssltest.py
https://gist.github.com/takeshixx/10107280
5.2) https://raw.githubusercontent.com/HackerFantastic/Public/master/exploits/heartbleed.c
5.3) https://github.com/robertdavidgraham/heartleech
6) Online Tests: (have you wondered what are they doing with the logs? ;)
6.1) http://filippo.io/Heartbleed/
6.2) http://possible.lv/tools/hb/
6.3) https://www.ssllabs.com/ssltest/
6.4) http://heartbleed.criticalwatch.com/
6.5) https://lastpass.com/heartbleed/
7) How bad is this? What the bad guys are doing?
7.1) Bruce Schneier - the crypto and security expert responsible for coining the term Security Theater: "practice of investing in countermeasures intended to provide the feeling of improved security while doing little or nothing to actually achieve it." - is saying that "Heartbleed is a catastrophic bug in OpenSSL" and that "Catastrophic" is the right word. On the scale of 1 to 10, this is an 11."
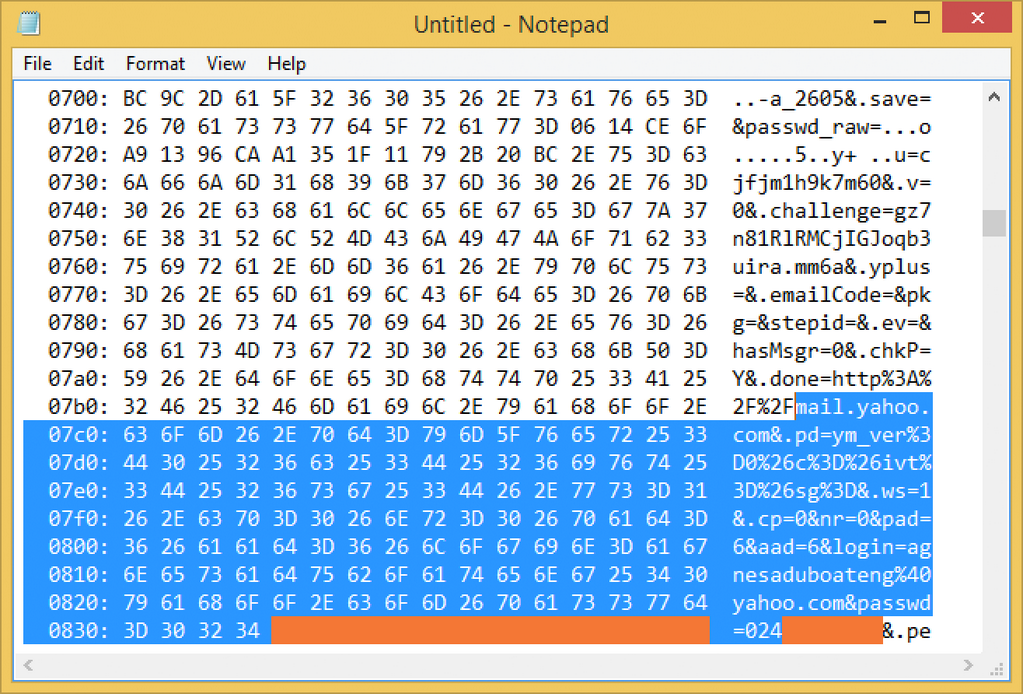
7.2) Well, right now many online services offered via HTTPS are not patched yet. So, if you login to Yahoo for example (check yahoo.com:443 in any test above), you can have you information (including user/password) read in plain text by an attacker:
7.3) One can also hijack user sessions exploiting the vulnerability.
7.4) In theory, you can dump the private key from the server, but was not fully demonstrated yet. There is a video showing the beginning of a private key being leaked by the heartbleed attack - but not all of it: https://www.youtube.com/watch?v=4fX-unvgMVU
8) Who / What is vulnerable?
8.1) 3 days after the official Heartbleed announcement, 78% of the initially vulnerable services are still exploitable: http://istheinternetfixedyet.com/
8.2) More than 600,000 sites are vulnerable: http://blog.erratasec.com/2014/04/600000-servers-vulnerable-to-heartbleed.htm
8.2) Companies are patching the vulnerability, but at least half million sites are vulnerable. (and other services like SSL VPNs, Webmails, etc.)
8.3) List of vendor notifications by The Sans Institute: https://isc.sans.edu/forums/diary/Heartbleed+vendor+notifications/17929
8.4) List of vulnerable Top Alexa 1000 sites (yahoo, imgur, flickr, redtube, archive.org, okcupid,...): https://github.com/musalbas/heartbleed-masstest/blob/master/top1000.txt
8.5) As expected, there are many mass tests running right now: https://zmap.io/heartbleed/ (including a link to the Alexa Top 1 million sites that are vulnerable)
8.6) There is an interesting list of big sites that have patched the Heartbleed bug maintained by @MrCippy: http://www.cnet.com/how-to/which-sites-have-patched-the-heartbleed-bug/
8.7) The most simple and common attack vector is from a client to a server, but the reverse is also possible. Enter "ReverseHeartBleed":https://reverseheartbleed.com/ Blog post: http://blog.meldium.com/home/2014/4/10/testing-for-reverse-heartbleed
8.8) Routers are also vulnerable, check the list of products affected from Cisco: http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed and Juniper: http://kb.juniper.net/InfoCenter/index?page=content&id=JSA10623
9) IDS rules to detect the abuse of this vulnerability:
9.1) Snort: http://blog.fox-it.com/2014/04/08/openssl-heartbleed-bug-live-blog/
9.2) Suricata: http://blog.inliniac.net/2014/04/08/detecting-openssl-heartbleed-with-suricata/
9.3) As you (should) know, IDS are easily bypassed (check item 5.3 above).
9.4) Bro-IDS is not bypassed by this: https://gist.github.com/sethhall/10436578 - detector: https://github.com/bro/bro/blob/topic/bernhard/heartbeat/scripts/policy/protocols/ssl/heartbleed.bro
10) How to detect successful Heartbleed attacks with tshark (thanks to @netresec):
$ tshark -i eth0 -R "ssl.record.content_type eq 24 and not ssl.heartbeat_message.type"
11) Nmap NSE plugin to check for the heartbleed vulnerability: https://svn.nmap.org/nmap/scripts/ssl-heartbleed.nse
Usage: $ nmap -p 21,990,1194,443,8443,993,995,465,4430 -sC –script heartbleed.nse 192.168.0.1-255
12) Important: if your servers are vulnerable, you have to patch them now and generate a new private key + certificate AND revoke the old certificate (and replace any other important info that might have been leaked before you patch - even reset user passwords if you are not sure). This was confirmed on 04/11/2014: https://www.cloudflarechallenge.com/heartbleed - credits: @indutny from Russia: https://gist.github.com/indutny/a11c2568533abcf8b9a1 and Ilkka Mattila from Finland CERT).
Happy patching! Detailed steps:
7 steps to stop the Heartbleed SSL/TLS bug (thanks to @datarisk article)
- Inventory all systems and servers running OpenSSL 1.0.1 and newer
- Upgrade to OpenSSL 1.0.1g or recompile with -DOPENSSL_NO_HEARTBEATS
- Revoke compromised keys and reissue new keys from the Certificate Authority
- Change user passwords and encryption keys
- All session keys and session cookies must be expired/invalidated
- All users of systems where SSL is in use must be informed of the potential for compromise
- Consider implementing perfect forward secrecy to protect against current and future attack
- Ensure that remediation efforts are carried out by qualified IT professionals
- Consider it a project – enforce accountability along with proper planning & documentation
- Aim for completeness – vulnerable OpenSSL distributions run on at least eight operating systems
- Take appropriate precautions to avoid business interruptions during the process
- Have the remediation efforts independently validated and get a written report
13.1) Chrome:
https://chrome.google.com/webstore/detail/chromebleed/eeoekjnjgppnaegdjbcafdggilajhpic
13.2) Firefox:
https://addons.mozilla.org/en-US/firefox/addon/foxbleed/
14) Want more information? Here are some good writeups on the Heartbleed bug:
14.1) Technical Writeups:
http://blog.cryptographyengineering.com/2014/04/attack-of-week-openssl-heartbleed.html
http://blog.existentialize.com/diagnosis-of-the-openssl-heartbleed-bug.html
14.2) Technical Video on the High-Level Mechanics of HeartBleed by @elastica:
http://vimeo.com/91425662
14.3) Non-Technical Writeups:
http://arstechnica.com/security/2014/04/critical-crypto-bug-in-openssl-opens-two-thirds-of-the-web-to-eavesdropping/
http://krebsonsecurity.com/2014/04/heartbleed-bug-exposes-passwords-web-site-encryption-keys/
14.4) Easy to understand videos:
by Mashable: https://www.youtube.com/watch?v=8oI_laHhGjE
by @jesperjurcenoks: https://www.youtube.com/watch?v=oZqXt0iddDQ
15) The HeartBleed bug was "discovered" now, but it is more than 2 years old, so..
15.1) Were Intelligence Agencies Using Heartbleed in November 2013?
https://www.eff.org/deeplinks/2014/04/wild-heart-were-intelligence-agencies-using-heartbleed-november-2013
15.2) NSA Said to Exploit Heartbleed Bug for Intelligence for Years
http://www.bloomberg.com/news/2014-04-11/nsa-said-to-have-used-heartbleed-bug-exposing-consumers.html
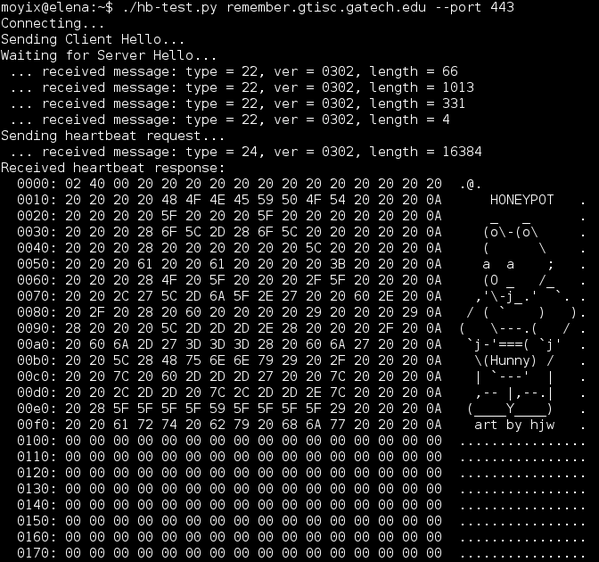
16) Anyway, a lot of people are now testing / scanning / mass scanning the whole internet for the Honeybleed bug. There's now a non-official / funny patch made by @moyix to use if you plan to run a vulnerable openssl honeypot:
http://remember.gtisc.gatech.edu/~brendan/honeybleed.patch
17) Well, if you read all this and are not impressed or worried, see this:
18) Credits: Codenomicon and Google
19) Thanks to @briankrebs, @steveD3, @CSOonline, @NetworkWorld and @ComputerWorld for linking to this re-cap on their blog posts / articles:
- http://krebsonsecurity.com/2014/04/heartbleed-bug-exposes-passwords-web-site-encryption-keys/
- http://www.csoonline.com/article/2141092/network-security/vendors-and-administrators-scramble-to-patch-openssl-vulnerability.html
- http://www.networkworld.com/news/2014/040814-vendors-and-administrators-scramble-to-280520.html?page=2